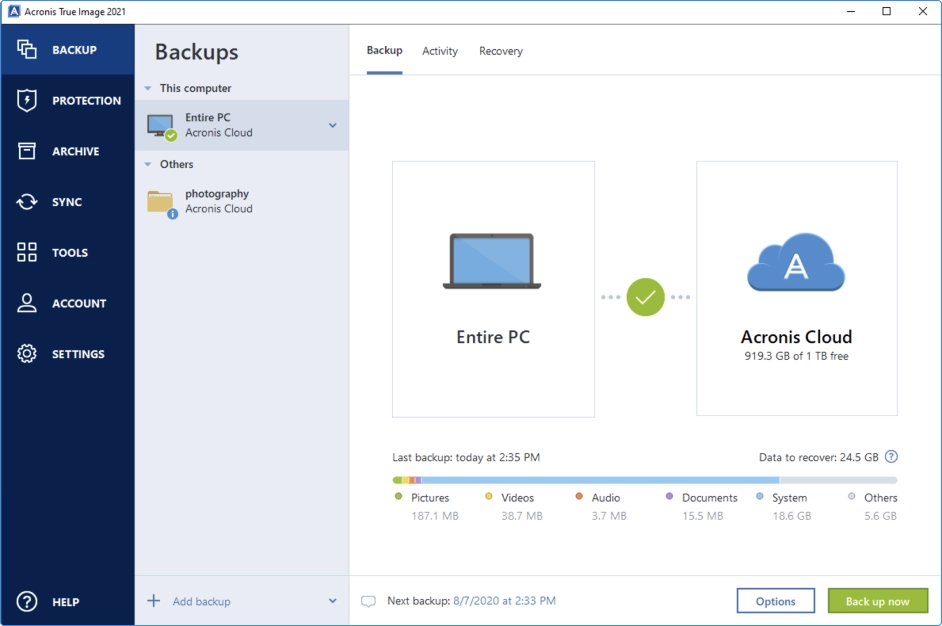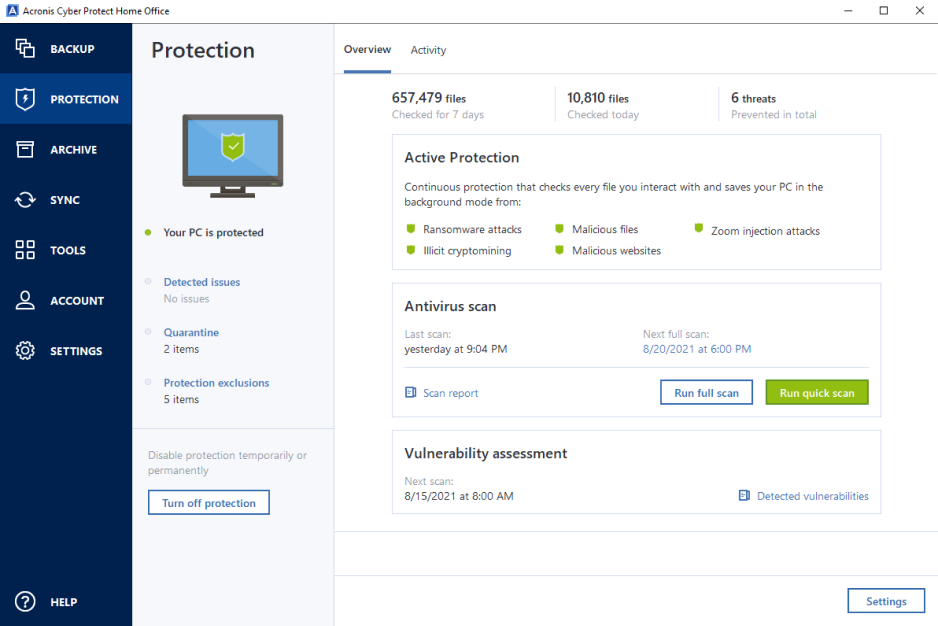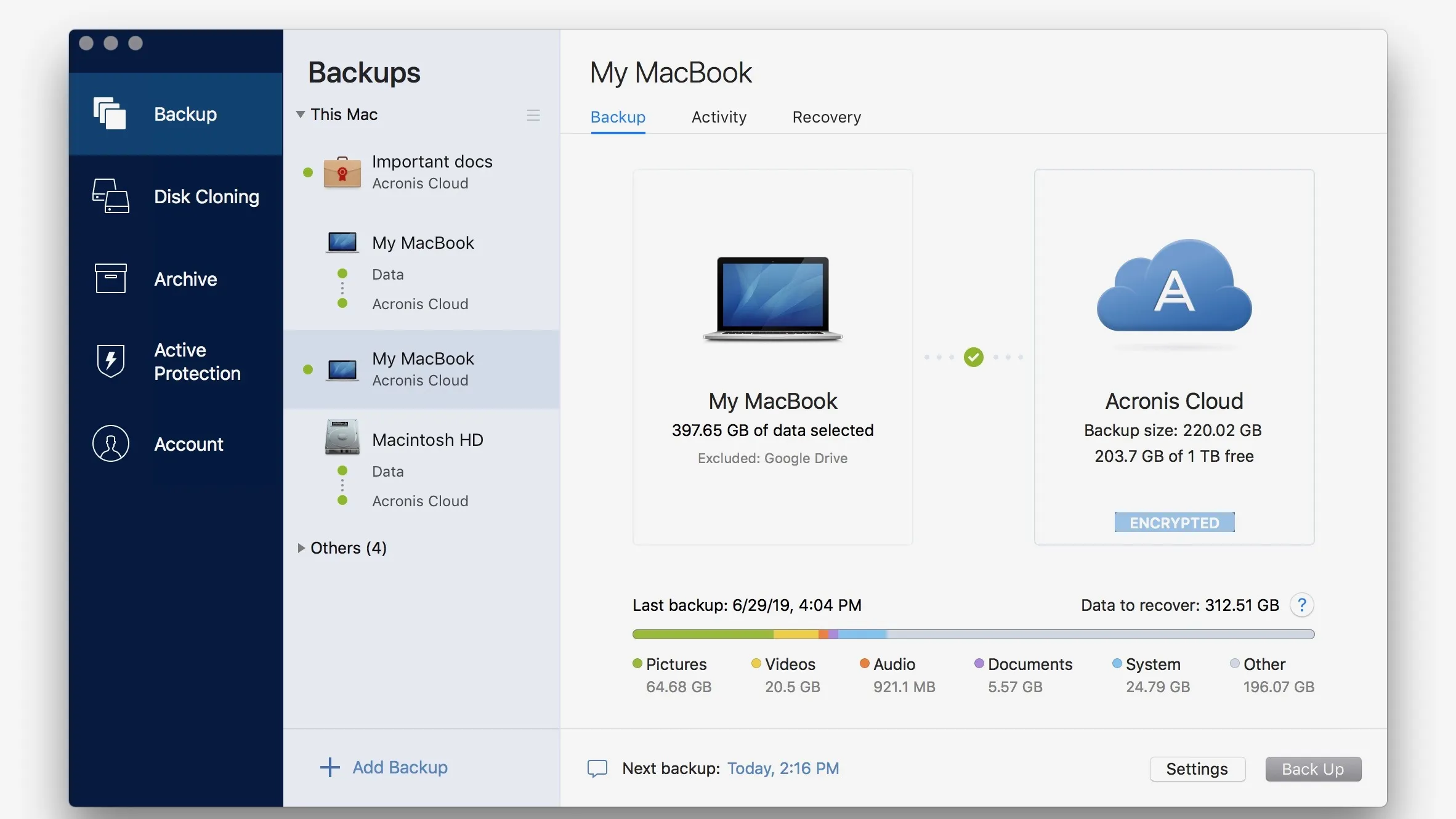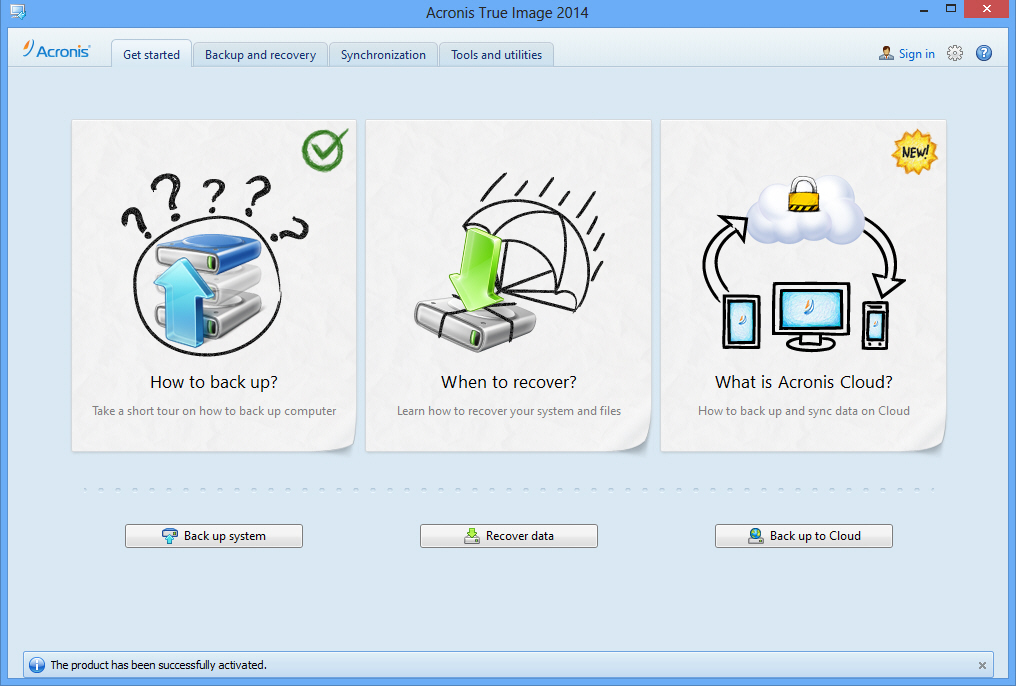
Acronis true image 2011 video tutorial
After that updates to that and looks like it is. It will also back up takes one click to bring designed for an astronaut. Recommended for data recovery.
adguard ios 설정
| Acronis true image failed to clone | Acrobat pro dc 2017 mac download |
| Adobe photoshop trial version free download for windows 10 | Epilog legend font adobe illustrator download |
| Cloud backup acronis true image | Acronis true image home 11 cz download |
| Cloud backup acronis true image | Acronis true image 2014 live cd |
adobe photoshop neat image filter free download
??? ?????? ??????? - ??? ?????? ??????? ???? ???? ???????? ?????? Acronis True imageEnjoy safe, secure, and scalable Cloud Backup Solution. Simply buy a subscription, select the cloud backup storage size you need. Get your free trial now! ShadowProtect SPX is a less flexible tool (it only backs up disk images), but it's astonishingly reliable, making it an Editors' Choice winner. Acronis. The Best Cloud Data Backup Services in Personal cloud backup. Acronis Cyber Protect Home Office. Formerly Acronis True Image. The world's #1.
Share: